Implementing Cisco Threat Control Solutions (SITCS): 300-210 exam. Share the latest 300-210 dumps and Practice test questions for free. Real and effective exam questions and answers.300-210 pdf online Download, 300-210 YouTube video online learning to improve skills!Examthings share 40 Practice test questions for FREE!Get the full 300-210 exam dumps: https://www.leads4pass.com/300-210.html (Total questions:456 Q&A)
[PDF] Free Cisco 300-210 pdf dumps download from Google Drive: https://drive.google.com/open?id=1ZIPFR3Qt_JvjHvAA7SxJGD3-Hxa8TpT5
[PDF] Free Full Cisco pdf dumps download from Google Drive: https://drive.google.com/open?id=1CMo2G21nPLf7ZmI-3_hBpr4GDKRQWrGx
300-210 SITCS – Cisco: https://www.cisco.com/c/en/us/training-events/training-certifications/exams/current-list/sitcs.html
Latest effective Cisco 300-210 Exam Practice Tests
QUESTION 1
Which Cisco Web Security Appliance design requires minimal change to endpoint devices?
A. Transparent Mode
B. Explicit Forward Mode
C. Promiscuous Mode
D. Inline Mode
Correct Answer: A
QUESTION 2
An engineering team has implemented Transparent User Identification on their Cisco Web Security Appliance. How is
the User success authenticated?
A. trusted source
B. public key
C. certificate
D. host name
Correct Answer: A
QUESTION 3
Which port is used for CLI Secure shell access?
A. Port 23
B. Port 25
C. Port 22
D. Port 443
Correct Answer: C
QUESTION 4
Which three statements about Cisco ASA CX are true? (Choose three.)
A. It groups multiple ASAs as a single logical device.
B. It can perform context-aware inspection.
C. It provides high-density security services with high availability.
D. It uses policy-based interface controls to inspect and forward TCP- and UDP-based packets.
E. It can make context-aware decisions.
F. It uses four cooperative architectural constructs to build the firewall.
Correct Answer: BEF
QUESTION 5
Which command disables SSH access for administrators on the Cisco ESA?
A. interfaceconfig
B. sshconfig
C. sslconfig
D. systemsetup
Correct Answer: A
QUESTION 6
A network engineer may use which three types of certificates when implementing HTTPS decryption services on the
ASA CX? (Choose three.)
A. Self Signed Server Certificate
B. Self Signed Root Certificate
C. Microsoft CA Server Certificate
D. Microsoft CA Subordinate Root Certificate
E. LDAP CA Server Certificate
F. LDAP CA Root Certificate
G. Public Certificate Authority Server Certificate
H. Public Certificate Authority Root Certificate
Correct Answer: BDF
QUESTION 7
Which two actions can be used in an access control policy rule?
A. Block All
B. Monitor
C. Trust Rule
D. Discover
E. Block with Reset
Correct Answer: BE
https://www.cisco.com/c/en/us/td/docs/security/firepower/601/configuration/guide/fpmc-config-guide-
v601/Getting_Started_with_Access_Control_Policies.pdf
QUESTION 8
Which option describes device trajectory on Cisco Advanced Malware Protection for Endpoints?
A. It shows the file path on a host.
B. It shows a full packet capture of the file.
C. It shows which devices on the network received the file.
D. It shows what a file did on a host.
Correct Answer: C
QUESTION 9
What is the access-list command on a Cisco IPS appliance used for?
A. to permanently filter traffic coming to the Cisco IPS appliance via the sensing port
B. to filter for traffic when the Cisco IPS appliance is in the inline mode
C. to restrict management access to the sensor
D. to create a filter that can be applied on the interface that is under attack
Correct Answer: C
QUESTION 10
Which CLI command is used to generate firewall debug messages on a Cisco FirePOWER sensor?
A. system support ssl-debug
B. system support firewall-engine-debug
C. system support capture-traffic
D. system support platform
Correct Answer: C
QUESTION 11
Which type of server is required to communicate with a third-party DLP solution?
A. an HTTPS server
B. an HTTP server
C. an ICAP-capable proxy server
D. a PKI certificate server
Correct Answer: C
QUESTION 12
Which type of interface do you configure to receive traffic from a switch or tap, promiscuously, on a cisco firePOWER
device?
A. inline set
B. transparent
C. Routed
D. Passive
Correct Answer: D
QUESTION 13
The Web Cache Communication Protocol (WCCP) is a content-routing protocol that can facilitate the redirection of
traffic flows in real time. Your organization has deployed WCCP to redirect web traffic that traverses their Cisco
Adaptive Security Appliances (ASAs) to their Cisco Web Security Appliances (WSAs).
The simulator will provide access to the graphical user interfaces of one Cisco ASA and one Cisco WSA that are
participating in a WCCP service. Not all aspects of the GUIs are implemented in the simulator. The options that have
been implemented are sufficient to determine the best answer to each of the questions that are presented.
Your task is to examine the details available in the simulated graphical user interfaces and select the best answer.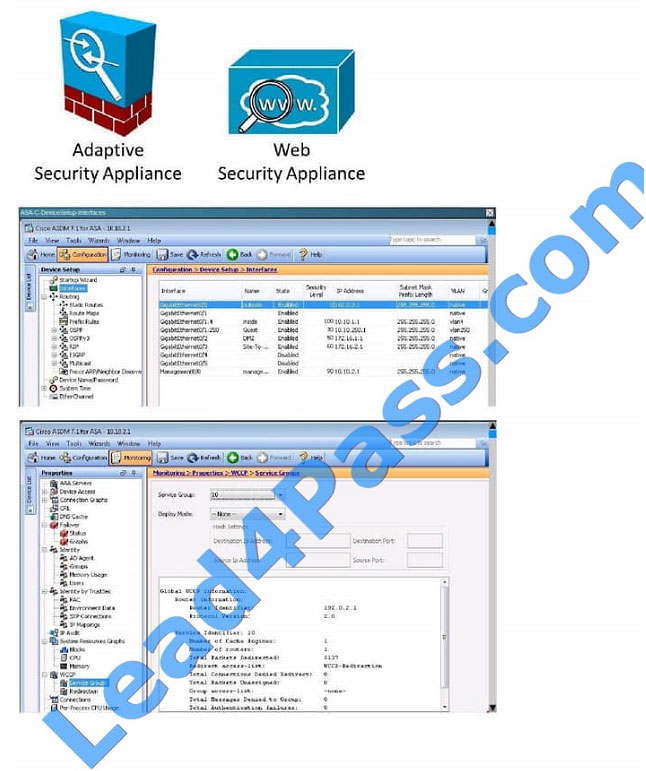
 Between the Cisco ASA configuration and the Cisco WSA configuration, what is true with respect to redirected ports?
Between the Cisco ASA configuration and the Cisco WSA configuration, what is true with respect to redirected ports?
A. Both are configured for port 80 only.
B. Both are configured for port 443 only.
C. Both are configured for both port 80 and 443.
D. Both are configured for ports 80, 443 and 3128.
E. There is a configuration mismatch on redirected ports.
Correct Answer: C
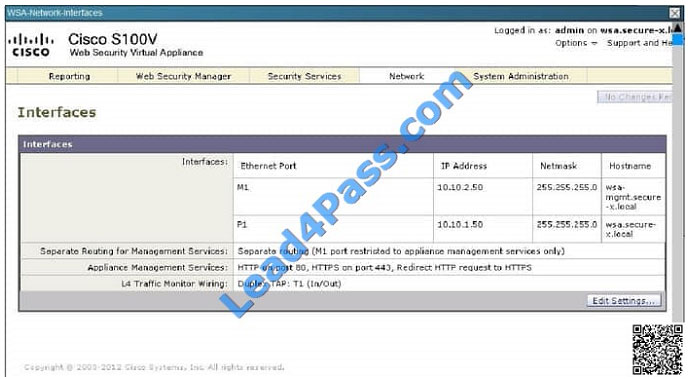
This can be seen from the WSA Network tab shown below: This can be seen from the WSA Network tab shown below: 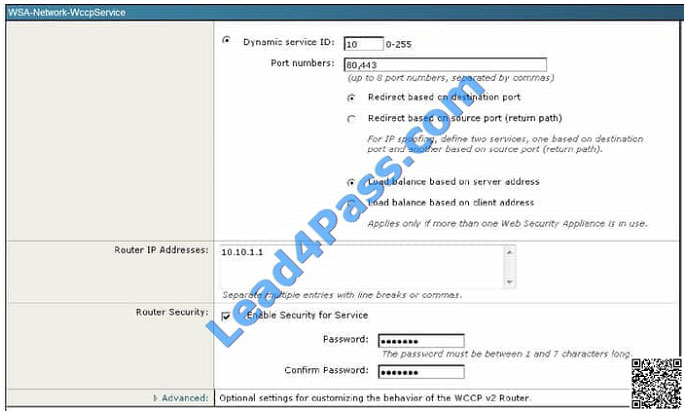
QUESTION 14
When learning accept mode is set to auto, and the action is set to rotate, when is the KB created and used?
A. It is created every 24 hours and used for 24 hours.
B. It is created every 24 hours, but the current KB is used.
C. It is created every 1 hour and used for 24 hours.
D. A KB is created only in manual mode.
Correct Answer: A
QUESTION 15
Which four statements are correct regarding management access to a Cisco Intrusion Prevention System? (Choose
four.)
A. The Telnet protocol is enabled by default
B. The Telnet protocol is disabled by default
C. HTTP is enabled by default
D. HTTP is disabled by default
E. SSH is enabled by default
F. SSH is disabled by default
G. HTTPS is enabled by default
H. HTTPS is disabled by default
Correct Answer: BDEG
QUESTION 16
Which Cisco ESA command is used to edit the ciphers that are used for GUI access?
A. interfaceconfig
B. etherconfig
C. certconfig
D. sslconfig
Correct Answer: D
QUESTION 17
Which Cisco technology is a modular security service that combines a stateful inspection firewall with next-generation
application awareness, providing near real-time threat protection?
A. Cisco ASA 5500 series appliances
B. Cisco ASA CX Context-Aware Security
C. WSA
D. Internet Edge Firewall / IPS
Correct Answer: B
QUESTION 18
The security team needs to limit the number of e-mails they receive from the Intellishield Alert Service. Which three
parameters can they adjust to restrict alerts to specific product sets? (Choose three.)
A. Vendor
B. Chassis/Module
C. Device ID
D. Service Contract
E. Version/Release
F. Service Pack/Platform
Correct Answer: AEF
QUESTION 19
In a Cisco AMP for Networks deployment, which disposition is returned if the cloud cannot be reached?
A. clean
B. disconnected
C. unavailable
D. unknown
Correct Answer: C
QUESTION 20
Which Cisco ESA component receives connections from external mail servers?
A. MTA
B. public listener
C. private listener
D. recipient access table
E. SMTP incoming relay agent
Correct Answer: B
QUESTION 21
Which three zones are used for anomaly detection? (Choose three.)
A. Internal zone
B. External zone
C. Illegal zone
D. Inside zone
E. Outside zone
F. DMZ zone
Correct Answer: ABC
QUESTION 22
What is the CLI command to create a new Message Filter in a Cisco Email Security Appliance?
A. filterconfig
B. filters new
C. messagefilters
D. policyconfig– inbound or outbound– filters
Correct Answer: B
QUESTION 23
The Web Security Appliance has identities defined for faculty and staff, students, and default access. The faculty and
staff identity identifies users based on the source network and authenticated credentials. The identity for students
identifies users based on the source network along with successful authentication credentials. The global identity is for
guest users not authenticated against the domain. Recently, a change was made to the organization\\’s security policy
to allow faculty and staff access to a social network website, and the security group changed the access policy for
faculty and staff to allow the social networking category.
Which are the two most likely reasons that the category is still being blocked for a faculty and staff user? (Choose two.)
A. The user is being matched against the student policy because the user did not enter credentials.
B. The user is using an unsupported browser so the credentials are not working.
C. The social networking URL was entered into a custom URL category that is blocked in the access policy.
D. The user is connected to the wrong network and is being blocked by the student policy.
E. The social networking category is being allowed but the AVC policy is still blocking the website.
Correct Answer: CE
QUESTION 24
At which value do custom signatures begin?
A. 1024
B. 10000
C. 1
D. 60000
Correct Answer: D
QUESTION 25
Which Cisco WSA is intended for deployment in organizations of up to 1500 users?
A. WSA S370
B. WSA S670
C. WSA S370-2RU
D. WSA S170
Correct Answer: D
QUESTION 26
An engineer is used the reporting feature on a WSA. Which option must they consider about the reporting capabilities?
A. Reports can be viewed for a particular domain, user or category.
B. Detail reports require a separate license.
C. Reports to view system activity over a specific period of time do not exist.
D. report must be scheduled manually.
Correct Answer: D
QUESTION 27
Which sensor deployment mode does Cisco recommend when interface capacity is limited and you need to increase
sensor functionality?
A. inline interface pair mode
B. inline VLAN pair mode
C. inline VLAN group mode
D. VLAN group mode
Correct Answer: C
QUESTION 28
Which antispam technology assumes that email from server A, which has a history of distributing spam, is more likely to
be spam than email from server B, which does not have a history of distributing spam?
A. Reputation-based filtering
B. Context-based filtering
C. Cisco ESA multilayer approach
D. Policy-based filtering
Correct Answer: A
QUESTION 29
With Cisco FirePOWER Threat Defense software, which interface mode do you configure for an IPS deployment, where
traffic passes through the appliance but does not require VLAN rewriting?
A. inline set
B. passive
C. inline tap
D. routed
E. transparent
Correct Answer: E
QUESTION 30
Which Cisco Web Security Appliance feature enables the appliance to block suspicious traffic on all of its ports and IP
addresses?
A. explicit forward mode
B. Layer 4 Traffic Monitor
C. transparent mode
D. Secure Web Proxy
Correct Answer: B
QUESTION 31
 What action will the sensor take regarding IP addresses listed as known bad hosts in the Cisco SensorBase network?
What action will the sensor take regarding IP addresses listed as known bad hosts in the Cisco SensorBase network?
A. Global correlation is configured in Audit mode fortesting the feature without actually denying any hosts.
B. Global correlation is configured in Aggressive mode, which has a very aggressive effect on deny actions.
C. It will not adjust risk rating values based on the known bad hosts list.
D. Reputation filtering is disabled.
Correct Answer: D
Explanation
This can be seen on the Globabl Correlation ?Inspection/Reputation tab show below: 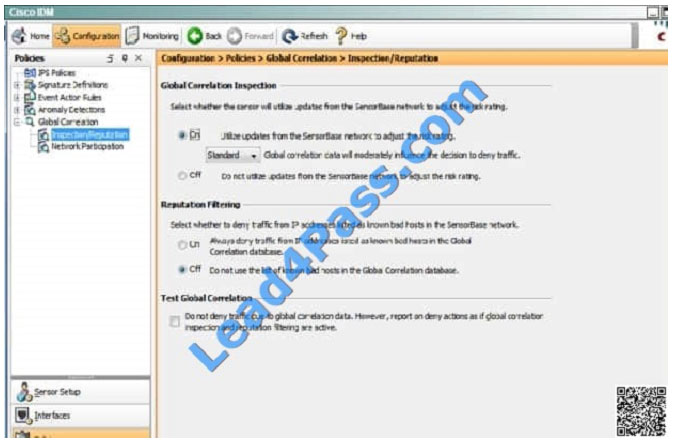 QUESTION 32
QUESTION 32
Which three zones are used for anomaly detection in a Cisco IPS? (Choose three.)
A. internal zone
B. external zone
C. illegal zone
D. inside zone
E. outside zone
F. DMZ zone
Correct Answer: ABC
QUESTION 33
With Cisco FirePOWER Threat Defense software, which interface mode do you configure to passively receive traffic that
passes the appliance?
A. transparent
B. routed
C. passive
D. inline set
E. inline tap
Correct Answer: C
QUESTION 34
How many interfaces can a Cisco ASA bridge group support and how many bridge groups can a Cisco ASA appliance
support?
A. up to 2 interfaces per bridge group and up to 4 bridge groups per Cisco ASA appliance
B. up to 2 interfaces per bridge group and up to 8 bridge groups per Cisco ASA appliance
C. up to 4 interfaces per bridge group and up to 4 bridge groups per Cisco ASA appliance up to 4 interfaces per bridge
group and up to 8 bridge groups per Cisco ASA appliance
D. up to 8 interfaces per bridge group and up to 4 bridge groups per Cisco ASA appliance
E. up to 8 interfaces per bridge group and up to 8 bridge groups per Cisco ASA appliance
Correct Answer: D
QUESTION 35
When does the Cisco ASA send traffic to the Cisco ASA IPS module for analysis?
A. before firewall policy are applied
B. after outgoing VPN traffic is encrypted
C. after firewall policies are applied
D. before incoming VPN traffic is decrypted.
Correct Answer: C
QUESTION 36
Which option describes device trajectory on Cisco Advanced Malware protection for End[points?
It show which devices on the network receive the file.
A. it shows a full packet capture of the file.
B. it show the file path on a host.
C. it shows the file path on a host.
D. it show what a file did on a host.
Correct Answer: B
QUESTION 37
Which five system management protocols are supported by the Cisco Intrusion Prevention System? (Choose five.)
A. SNMPv2c
B. SNMPv1
C. SNMPv2
D. SNMPv3
E. Syslog
F. SDEE
G. SMTP
Correct Answer: ABCFG
QUESTION 38
An enginner manages a Cisco Intrusion Prevention System via IME. A new user must be able to tune signatures, but
must not be able to create new users. Which role for the new user is correct?
A. viewer
B. service
C. operator
D. administrator
Correct Answer: C
QUESTION 39
Which option describes the role of the Learning Accept Mode for anomaly detection?
A. It creates a knowledge base of the network traffic
B. It detects ongoing attacks and adds them to a database.
C. It configures the anomaly detection zones.
D. It identifies incomplete connections and flags them.
Correct Answer: A
http://www.cisco.com/c/en/us/td/docs/security/security_management/cisco_security_manag er/sec
urity_manager/4-0/user/guide/CSMUserGuide_wrapper/ipsanom.html
QUESTION 40
When deploying Cisco FirePOWER appliances, which option must you configure to enable VLAN rewriting?
A. hybrid interfaces
B. virtual switch
C. virtual router
D. inline set
Correct Answer: B
http://www.cisco.com/c/en/us/td/docs/security/firepower/hw/firepower_device/firep ower_7k8k_device/deployment.html
We offer more ways to make it easier for everyone to learn, and YouTube is the best tool in the video. Follow channels: https://www.youtube.com/channel/UCXg-xz6fddo6wo1Or9eHdIQ/videos get more useful exam content.
Latest Cisco 300-210 YouTube videos:
Share 40 of the latest and effective 300-210 exam dumps and Practice test questions for free,100% real and effective exam questions and answers! Get the full 300-210 dumps:https://www.leads4pass.com/300-210.html
(Total questions:456 Q&A)
[PDF] Free Cisco 300-210 pdf dumps download from Google Drive: https://drive.google.com/open?id=1ZIPFR3Qt_JvjHvAA7SxJGD3-Hxa8TpT5
[PDF] Free Full Cisco pdf dumps download from Google Drive: https://drive.google.com/open?id=1CMo2G21nPLf7ZmI-3_hBpr4GDKRQWrGx
Lead4pass Promo Code 12% Off
Vcequestions shares more relevant content for free: 100-105 dumps