Lead4Pass 200-201 dumps page: https://www.leads4pass.com/200-201.html, including both PDF and VCE study modes, the most popular study tool now, can help you easily succeed in the 200-201 CBROPS exam. Cisco 200-201 CBROPS subject matter experts have developed 245 200-201 dumps of exam questions and answers based on the following core content:
- Security concepts
- Security monitoring
- Host-based analysis
- Network intrusion analysis
- Security policies and procedures
Having a Lead4Pass 200-201 dumps PDF file or dumps VCE engine is the best option for taking the 200-201 CBROPS exam. These 200-201 dumps questions cover the real “200-201 CBROPS Threat Hunting and Defending using Cisco Technologies for CyberOps” Each topic of the certification exam. So getting the full pass exam questions and answers from the Lead4Pass 200-201 dumps will help you pass the 200-201 CBROPS exam on your first attempt, ensuring excellent end results.
What you need to know about the 200-201 CBROPS exam:
Candidates should know the details of the 200-201 CBROPS exam. Here are some basics.
200-201 CBROPS exam is short for Threat Hunting and Defending using Cisco Technologies for CyberOps (CBROPS), 200-201 is the exam code, more details are shown below:
Vendor: Cisco
Exam Code: 200-201
Exam Name: Threat Hunting and Defending using Cisco Technologies for CyberOps (CBROPS)
Certification: CyberOps Associate
Duration: 120 minutes
Languages: English
Price: $300 USD
Give you some of the 200-201 dumps exam questions
QUESTION 1:
Refer to the exhibit.
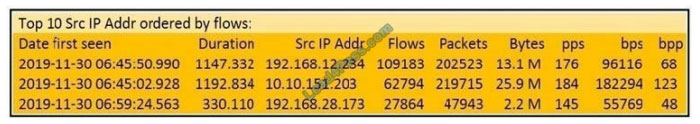
What information is depicted?
A. IIS data
B. NetFlow data
C. network discovery event
D. IPS event data
Correct Answer: B
QUESTION 2:
An intruder attempted malicious activity and exchanged emails with a user and received corporate information, including email distribution lists. The intruder asked the user to engage with a link in an email. When the fink launched, it infected machines and the intruder was able to access the corporate network.
Which testing method did the intruder use?
A. social engineering
B. eavesdropping
C. piggybacking
D. tailgating
Correct Answer: A
QUESTION 3:
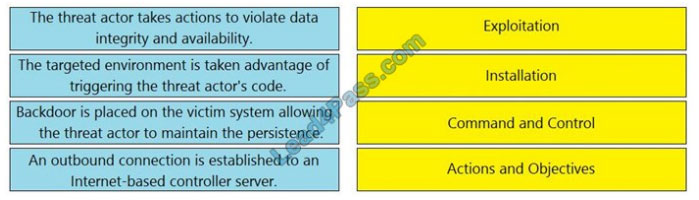
DRAG-DROP
Drag and drop the definition from the left onto the phase on the right to classify intrusion events according to the Cyber Kill Chain model.
Select and Place:
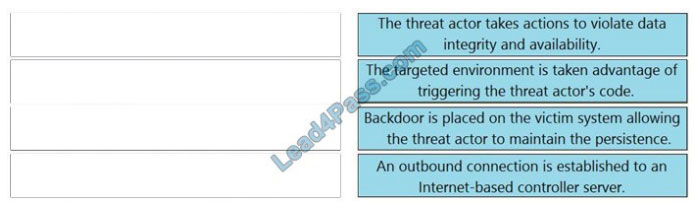
Correct Answer:
QUESTION 4:
What is an example of social engineering attacks?
A. receiving an unexpected email from an unknown person with an attachment from someone in the same company
B. receiving an email from human resources requesting a visit to their secure website to update contact information
C. sending a verbal request to an administrator who knows how to change an account password
D. receiving an invitation to the department\’s weekly WebEx meeting
Correct Answer: C
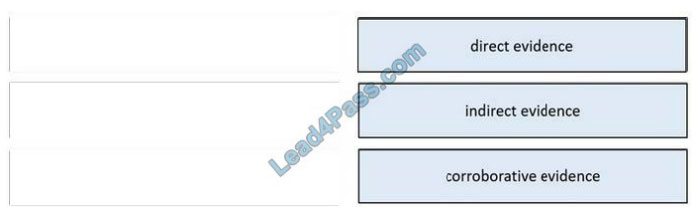
QUESTION 5:
DRAG-DROP
Drag and drop the type of evidence from the left onto the description of that evidence on the right.
Select and Place:
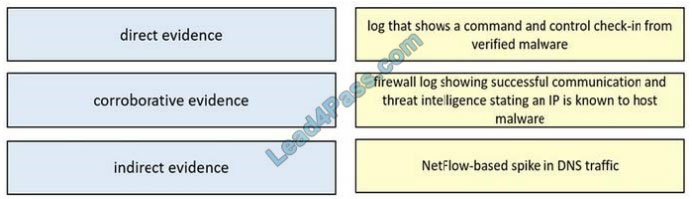
Correct Answer:
QUESTION 6:
How does an SSL certificate impact security between the client and the server?
A. by enabling an authenticated channel between the client and the server
B. by creating an integrated channel between the client and the server
C. by enabling an authorized channel between the client and the server
D. by creating an encrypted channel between the client and the server
Correct Answer: D
QUESTION 7:
A security expert is working on a copy of the evidence, an ISO file that is saved in CDFS format. Which type of evidence is this file?
A. CD data copy prepared in Windows
B. CD data copy prepared in Mac-based system
C. CD data copy prepared in Linux system
D. CD data copy prepared in Android-based system
Correct Answer: A
QUESTION 8:
Refer to the exhibit.
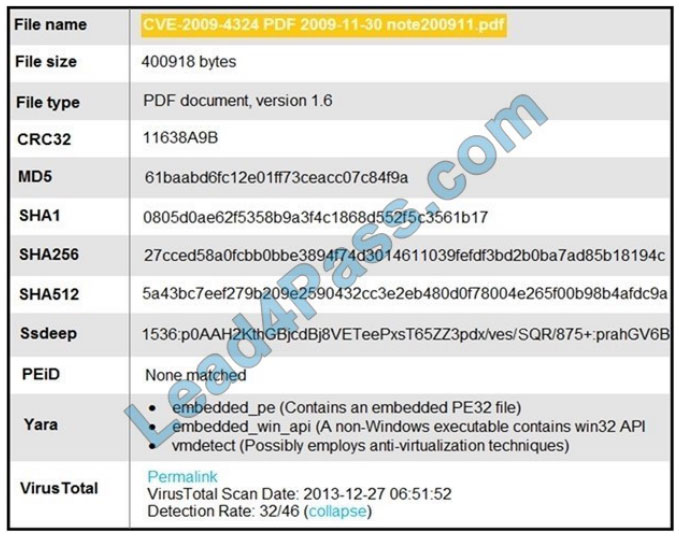
An engineer is analyzing this Cuckoo Sandbox report for a PDF file that has been downloaded from an email. What is the state of this file?
A. The file has an embedded executable and was matched by PEiD threat signatures for further analysis.
B. The file has an embedded non-Windows executable but no suspicious features are identified.
C. The file has an embedded Windows 32 executable and the Yara field lists suspicious features for further analysis.
D. The file was matched by PEiD threat signatures but no suspicious features are identified since the signature list is up to date.
Correct Answer: C
QUESTION 9:
Refer to the exhibit.
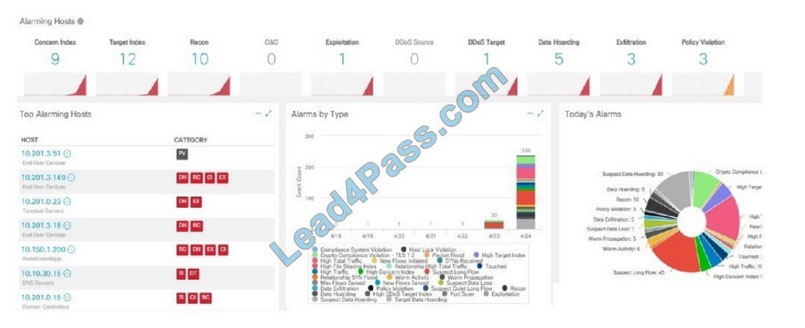
What is the potential threat identified in this Stealthwatch dashboard?
A. A policy violation is active for host 10.10.101.24.
B. A host on the network is sending a DDoS attack to another inside host.
C. There are three active data exfiltration alerts.
D. A policy violation is active for host 10.201.3.149.
Correct Answer: C
“EX” = exfiltration
And there are three.
Also the “suspect long flow” and “suspect data heading” suggest, for example, DNS exfiltration
https://www.cisco.com/c/dam/en/us/td/docs/security/stealthwatch/management_console/sm
c_users_guide/SW_6_9_0_SMC_Users_Guide_DV_1_2.pdf page 177.
QUESTION 10:
A company is using several network applications that require high availability and responsiveness, such that milliseconds of latency on network traffic is not acceptable. An engineer needs to analyze the network and identify ways to improve traffic movement to minimize delays. Which information must the engineer obtain for this analysis?
A. total throughput on the interface of the router and NetFlow records
B. output of routing protocol authentication failures and ports used
C. running processes on the applications and their total network usage
D. deep packet captures of each application flow and duration
Correct Answer: C
QUESTION 11:
DRAG-DROP
Drag and drop the security concept on the left onto the example of that concept on the right.
Select and Place:
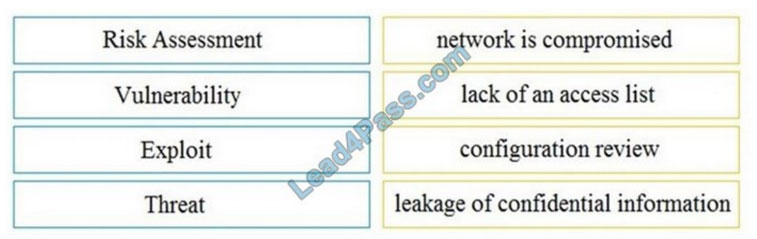
Correct Answer:

QUESTION 12:
What is an attack surface as compared to a vulnerability?
A. any potential danger to an asset
B. the sum of all paths for data into and out of the environment
C. an exploitable weakness in a system or its design
D. the individuals who perform an attack
Correct Answer: C
An attack surface is the total sum of vulnerabilities that can be exploited to carry out a security attack. Attack surfaces can be physical or digital. The term attack surface is often confused with the term attack vector, but they are not the same thing. The surface is what is being attacked; the vector is the means by which an intruder gains access.
QUESTION 13:
What is obtained using NetFlow?
A. session data
B. application logs
C. network downtime report
D. full packet capture
Correct Answer: A
……
The above 200-201 dumps exam questions can be downloaded online:https://drive.google.com/file/d/1Hq9tXhs7kyJzL3cTTXNNYoTOKZOld2X7/view?usp=sharing
View 245 questions:

13 200-201 dumps exam questions to help you understand part of the “200-201 CBROPS Understanding Cisco Cybersecurity Operations Fundamentals” exam content.
The Lead4Pass 200-201 dumps contain 245 complete exam questions and answers, truly ensuring your success in passing the 200-201 CBROPS exam.