The best and most updated latest CompTIA Security+ SY0-401 dumps exam training materials in PDF format free download from leads4pass. “CompTIA Security+ Certification” is the name of CompTIA Security+ https://www.leads4pass.com/sy0-401.html exam dumps which covers all the knowledge points of the real CompTIA exam. High quality CompTIA Security+ SY0-401 dumps pdf files and vce youtube demo free shared.
Latest CompTIA Security+ SY0-401 dumps exam questions and answers free download from leads4pass. Useful latest CompTIA Security+ SY0-401 dumps pdf training resources which are the best for clearing SY0-401 exam test, and to get certified by CompTIA Security+.
High quality CompTIA SY0-401 dumps pdf materials free download: https://drive.google.com/open?id=0B_7qiYkH83VRMEhpY1lTQnR4NDA
High quality CompTIA SY0-101 dumps pdf materials free download: https://drive.google.com/open?id=0B_7qiYkH83VRWm1VeWl0ZVhINkk
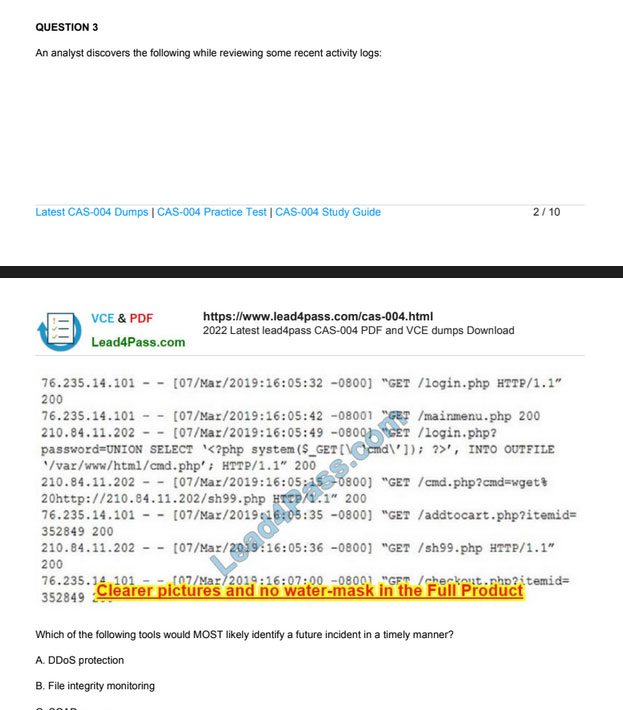
QUESTION 1
The Chief Information Officer (CIO) receives an anonymous threatening message that says andquot;beware of the 1st of the yearandquot;. The CIO suspects the message may be from a former disgruntled employee planning an attack.
Which of the following should the CIO be concerned with?
A. Smurf Attack
B. Trojan
C. Logic bomb
D. Virus
Correct Answer: C
QUESTION 2
Two organizations want to share sensitive data with one another from their IT systems to support a mutual customer base. Both organizations currently have secure network and security policies and procedures. Which of the following should be the PRIMARY security considerations by the security managers at each organization prior to sharing information? (Select THREE)
A. Physical security controls
B. Device encryption
C. Outboarding/Offboarding
D. Use of digital signatures
E. SLA/ISA
F. Data ownership
G. Use of smartcards or common access cards
H. Patch management
Correct Answer: BEF
QUESTION 3
Sara, a security engineer, is testing encryption ciphers for performance. Which of the following ciphers offers strong encryption with the FASTEST speed?
A. 3DES
B. Blowfish
C. Serpent
D. AES256
Correct Answer: B
QUESTION 4
Ann, a security administrator at a call center, has been experiencing problems with users intentionally installing unapproved and occasionally malicious software on their computers. SY0-401 dumps Due to the nature of their jobs, Ann cannot change their permissions. Which of the following would BEST alleviate her concerns?
A. Deploy a HIDS suite on the users\’ computer to prevent application installation
B. Maintain the baseline posture at the highest OS patch level
C. Enable the pop-up blockers on the user\’s browsers to prevent malware
D. Create an approved application list and block anything not on it
Correct Answer: D
QUESTION 5
The IT department has been tasked with reducing the risk of sensitive information being shared with unauthorized entities from computers it is saved on, without impeding the ability of the employees to access the internet.
Implementing which of the following would be the best way to accomplish this objective?
A. Host-based firewalls
B. DLP
C. URL filtering
D. Pop-up blockers
Correct Answer: B
QUESTION 6
Ann, the network administrator, has learned from the helpdesk that employees are accessing the wireless network without entering their domain credentials upon connection. Once the connection is made, they cannot reach any internal resources, while wired network connections operate smoothly. Which of the following is MOST likely occurring?
A. A user has plugged in a personal access point at their desk to connect to the network wirelessly.
B. The company is currently experiencing an attack on their internal DNS servers.
C. The company\’s WEP encryption has been compromised and WPA2 needs to be implemented instead.
D. An attacker has installed an access point nearby in an attempt to capture company information.
Correct Answer: D
QUESTION 7
An application developer has coded a new application with a module to examine all user entries for the graphical user interface. The module verifies that user entries match the allowed types for each field and that OS and database commands are rejected before entries are sent for further processing within the application. These are example of:
A. Input validation
B. SQL injection
C. Application whitelisting
D. Error handling
Correct Answer: A
QUESTION 8
The finance department works with a bank which has recently had a number of cyber attacks. The finance department is concerned that the banking website certificates have been compromised. Which of the following can the finance department check to see if any of the bank\’s certificates are still valid?
A. Bank\’s CRL
B. Bank\’s private key
C. Bank\’s key escrow
D. Bank\’s recovery agent
Correct Answer: A
QUESTION 9
When using PGP, which of the following should the end user protect from compromise? SY0-401 dumps (Select TWO).
A. Private key
B. CRL details
C. Public key
D. Key password
E. Key escrow
F. Recovery agent
Correct Answer: AD
QUESTION 10
In order to enter a high-security datacenter, users are required to speak the password into a voice recognition system.
Ann a member if the sales department over hears the password and upon speaks it into the system. The system denies her entry and alerts the security team. Which of the following is the MOST likely reason for her failure to enter the data center?
A. An authentication factor
B. Discretionary access
C. Time of day restrictions
D. Least privilege restrictions
Correct Answer: A
QUESTION 11
Which of the following access control methodologies provides an individual with the most restrictive access rights to successfully perform their authorized duties?
A. Mandatory Access Control
B. Rule Based Access Control
C. Least Privilege
D. Implicit Deny
E. Separation of Duties
Correct Answer: C
QUESTION 12
Which of the following explains the difference between a public key and a private key?
A. The public key is only used by the client while the private key is available to all. Both keys are mathematically related.
B. The private key only decrypts the data while the public key only encrypts the data. Both keys are mathematically related.
C. The private key is commonly used in symmetric key decryption while the public key is used in asymmetric key decryption.
D. The private key is only used by the client and kept secret while the public key is available to all.
Correct Answer: D
QUESTION 13
A technician has been tasked with installing and configuring a wireless access point for the engineering department.
After the AP has been installed, there have been reports the employees from other departments have been connecting to it without approval. SY0-401 dumps Which of the following would BEST address these concerns?
A. Change the SSID of the AP so that it reflects a different department, obscuring its ownership
B. Implement WPA2 encryption in addition to WEP to protect the data-in-transit
C. Configure the AP to allow only to devices with pre-approved hardware addresses
D. Lower the antenna\’s power so that it only covers the engineering department\’s offices
Correct Answer: D
QUESTION 14
An internal audit has detected that a number of archived tapes are missing from secured storage. There was no recent need for restoration of data from the missing tapes. The location is monitored by access control and CCTV systems.
Review of the CCTV system indicates that it has not been recording for three months. The access control system shows numerous valid entries into the storage location during that time. The last audit was six months ago and the tapes were accounted for at that time. Which of the following could have aided the investigation?
A. Testing controls
B. Risk assessment
C. Signed AUP
D. Routine audits
Correct Answer: A
QUESTION 15
A software development company needs to share information between two remote server, using encryption to protect it.
A programmer suggests developing a new encryption protocol, arguing that using an unknown protocol with secure, existing cryptographic algorithem libraries will provide strong encryption without being susceptible to attacks on other unknown protocols. Which of the following summarizes the BEST response to programmer\’s proposal?
A. The newly developed protocol will not be as the underlying cryptographic algorithms used.
B. New protocols often introduce unexpected vulnerabilites, even when developed with otherwise secure and tested algorithm libraries.
C. A programmer should have specialized training in protocol development before attempting to design a new encryption protocol.
D. The obscurity value of unproven protocols against attacks often outweighs the potential for new vulnerabilites.
Correct Answer: D
The best helpful CompTIA Security+ https://www.leads4pass.com/sy0-401.html dumps pdf practice resources and study guides free update. High quality CompTIA Security+ SY0-401 dumps real exam questions and answers update free try, pass CompTIA SY0-401 exam test easily.
Useful latest CompTIA Security+ SY0-401 dumps vce youtube: https://youtu.be/Ti0gVvsg5eI