How do I get the latest free CompTIA CAS-003 exam practice questions?
Latest CAS-003 exam dump, CAS-003 pdf, online CompTIA CAS-003 practice test questions free to improve skills and experience,
98.5% of exam pass rate selection lead4Pass CAS-003 dumps: https://www.leads4pass.com/cas-003.html (latest update)
Latest Updated CompTIA CAS-003 video tutorial
CompTIA CAS-003 exam pdf free download
[PDF Q1-Q13] Free CompTIA CAS-003 pdf dumps download from Google Drive: https://drive.google.com/open?id=1MM-PdW6DeFCHWCw3ojyatuurqMkoXSSn
CompTIA CASP+ CAS-003 Certification Study Guide: https://www.comptia.org/training/books/casp-cas-003-study-guide
Latest effective CompTIA CAS-003 exam practice questions
QUESTION 1
A Chief Information Officer (CIO) publicly announces the implementation of a new financial system. As part of a security
assessment that includes a social engineering task, which of the following tasks should be conducted to demonstrate
the BEST means to gain information to use for a report on social vulnerability details about the financial system?
A. Call the CIO and ask for an interview, posing as a job seeker interested in an open position
B. Compromise the email server to obtain a list of attendees who responded to the invitation who is on the IT staff
C. Notify the CIO that, through observation at events, malicious actors can identify individuals to befriend
D. Understand the CIO is a social drinker, and find the means to befriend the CIO at establishments the CIO frequents
Correct Answer: D
QUESTION 2
During a security event investigation, a junior analyst fails to create an image of a server\\’s hard drive before removing
the drive and sending it to the forensics analyst. Later, the evidence from the analysis is not usable in the prosecution of
the attackers due to the uncertainty of tampering. Which of the following should the junior analyst have followed?
A. Continuity of operations
B. Chain of custody
C. Order of volatility
D. Data recovery
Correct Answer: C
QUESTION 3
The director of sales asked the development team for some small changes to increase the usability of an application
used by the sales team. Prior security reviews of the code showed no significant vulnerabilities, and since the changes
were small, they were given a peer review and then pushed to the live environment. Subsequent vulnerability scans now
show numerous flaws that were not present in the previous versions of the code. Which of the following is an SDLC best
practice that should have been followed?
A. Versioning
B. Regression testing
C. Continuous integration
D. Integration testing
Correct Answer: B
QUESTION 4
Ann, a systems engineer, is working to identify an unknown node on the corporate network. To begin her investigative
work, she runs the following Nmap command string: user@hostname:~$ Sudo Nmap 192.168.1.54 Based on the output,
Nmap is unable to identify the OS running on the node, but the following ports are open on the device: TCP/22 TCP/111
TCP/512-514 TCP/2049 TCP/32778 Based on this information, which of the following operating systems is MOST likely
running on the unknown node?
A. Linux
B. Windows
C. Solaris
D. OSX
Correct Answer: C
TCP/22 is used for SSH; TCP/111 is used for Sun RPC; TCP/512-514 is used by CMD like exec, but automatic
authentication is performed as with a login server, etc. These are all ports that are used when making use of the Sun
Solaris operating system.
QUESTION 5
An investigator wants to collect the most volatile data first in an incident to preserve the data that runs the highest risk of
being lost. After memory, which of the following BEST represents the remaining order of volatility that the investigator
should follow?
A. File system information, swap files, network processes, system processes, and raw disk blocks.
B. Raw disk blocks, network processes, system processes, swap files, and file system information.
C. System processes, network processes, file system information, swap files, and raw disk blocks.
D. Raw disk blocks, swap files, network processes, system processes, and file system information.
Correct Answer: C
The order in which you should collect evidence is referred to as the Order of volatility. Generally, evidence should be
collected from the most volatile to the least volatile. The order of volatility from most volatile to least volatile is as follows:
Data in RAM, including CPU cache and recently, used data and applications Data in RAM, including system and network
processes Swap files (also known as paging files) stored on local disk drives Data stored on local disk drives Logs
stored on remote systems Archive media
QUESTION 6
An organization wants to arm its cybersecurity defensive suite automatically with intelligence on zero-day threats shortly
after they emerge. Acquiring tools and services that support which of the following data standards would BEST enable
the organization to meet this objective?
A. XCCDF
B. OVAL
C. STIX
D. CWE
E. CVE
Correct Answer: E
QUESTION 7
A penetration tester is conducting an assessment on Comptia.org and runs the following command from a coffee shop
while connected to the public Internet: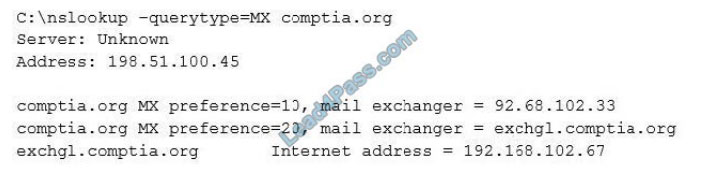
Which of the following should the penetration tester conclude about the command output?
A. The public/private views on the Comptia.org DNS servers are misconfigured
B. Comptia.org is running an older mail server, which may be vulnerable to exploits
C. The DNS SPF records have not been updated for Comptia.org
D. 192.168.102.67 is a backup mail server that may be more vulnerable to attack
Correct Answer: B
QUESTION 8
The Chief Information Officer (CIO) wants to increase security and accessibility among the organization\\’s cloud SaaS
applications. The applications are configured to use passwords, and two-factor authentication is not provided natively.
Which of the following would BEST address the CIO\\’s concerns?
A. Procure a password manager for the employees to use with the cloud applications.
B. Create a VPN tunnel between the on-premises environment and the cloud providers.
C. Deploy applications internally and migrate away from SaaS applications.
D. Implement an IdP that supports SAML and time-based, one-time passwords.
Correct Answer: B
QUESTION 9
A software development team is conducting functional and user acceptance testing of internally developed web
applications using a COTS solution. For automated testing, the solution uses valid user credentials from the enterprise
directory to authenticate to each application. The solution stores the username in plain text and the corresponding
password as an encoded string in a script within a file, located on a globally accessible network share. The account
credentials used to belong to the development team lead. To reduce the risks associated with this scenario while
minimizing disruption to ongoing testing, which of the following are the BEST actions to take? (Choose two.)
A. Restrict access to the network share by adding a group only for developers to the share\\’s ACL
B. Implement a new COTS solution that does not use hard-coded credentials and integrates with directory services
C. Obfuscate the username within the script file with encoding to prevent easy identification and the account used
D. Provision of a new user account within the enterprise directory and enable its use for authentication to the target
applications. Share the username and password with all developers for use in their individual scripts
E. Redesign the web applications to accept single-use, local account credentials for authentication
Correct Answer: AB
QUESTION 10
A security analyst is attempting to break into a client\\’s secure network. The analyst was not given prior information
about the client, except for a block of public IP addresses that are currently in use. After network enumeration, the
analyst\\’s NEXT step is to perform:
A. a gray-box penetration test
B. a risk analysis
C. a vulnerability assessment
D. an external security audit
E. a red team exercise
Correct Answer: A
QUESTION 11
Company ABC\\’s SAN is nearing capacity and will cause costly downtimes if servers run out disk space. Which of the
following is a more cost-effective alternative to buying a new SAN?
A. Enable multipath to increase the availability
B. Enable deduplication on the storage pools
C. Implement snapshots to reduce virtual disk size
D. Implement replication to offsite datacenter
Correct Answer: B
Storage-based data deduplication reduces the amount of storage needed for a given set of files. It is most effective in
applications where many copies of very similar or even identical data are stored on a single disk.
It is common for multiple copies of files to exist on a SAN. By eliminating (deduplicating) repeated copies of the files, we
can reduce the disk space used on the existing SAN. This solution is a cost-effective alternative to buying a new SAN.
QUESTION 12
The risk subcommittee of a corporate board typically maintains a master register of the most prominent risks to the
company. A centralized holistic view of risk is particularly important to the corporate Chief Information Security Officer
(CISO) because:
A. IT systems are maintained in silos to minimize interconnected risks and provide clear risk boundaries used to
implement compensating controls
B. risks introduced by a system in one business unit can affect other business units in ways in which the individual
business units have no awareness
C. corporate general counsel requires a single system boundary to determine overall corporate risk exposure
D. major risks identified by the subcommittee merit the prioritized allocation of scare funding to address cybersecurity
concerns
Correct Answer: A
QUESTION 13
A system owner has requested support from data owners to evaluate options for the disposal of equipment containing
sensitive data. Regulatory requirements state the data must be rendered unrecoverable via logical means or physically
destroyed. Which of the following factors is the regulation intended to address?
A. Sovereignty
B. E-waste
C. Remanence
D. Deduplication
Correct Answer: B
Share lead4Pass CompTIA CAS-003 Discount codes for free 2020

leads4pass Reviews
leads4pass offers the latest exam exercise questions for free! CompTIA exam questions are updated throughout the year.
leads4pass has many professional exam experts! Guaranteed valid passing of the exam! The highest pass rate, the highest cost-effective!
Help you pass the exam easily on your first attempt.

What you need to know:
Vcequestions shares the latest CompTIA CAS-003 exam dumps, CAS-003 pdf, CAS-003 exam exercise questions for free. You can improve your skills and exam experience online to get complete exam questions and answers guaranteed to pass the exam we recommend leads4pass CAS-003 exam dumps
Latest update leads4pass CAS-003 exam dumps: https://www.leads4pass.com/cas-003.html (530 Q&As)
[Q1-Q13 PDF] Free CompTIA CAS-003 pdf dumps download from Google Drive: https://drive.google.com/open?id=1MM-PdW6DeFCHWCw3ojyatuurqMkoXSSn